
Cybercriminals are exploiting a trick to turn off Apple iMessage’s built-in phishing protection for a text and trick users into re-enabling disabled phishing links.
With so much of our daily activities done from our mobile devices, whether paying bills, shopping, or communicating with friends and colleagues, threat actors increasingly conduct smishing (SMS phishing) attacks against mobile numbers.
To protect users from such attacks, Apple iMessage automatically disables links in messages received from unknown senders, whether that be an email address or phone number.
However, Apple told BleepingComputer that if a user replies to that message or adds the sender to their contact list, the links will be enabled.
Tricking users into replying
Over the past couple of months, BleepingComputer has seen a surge in smishing attacks that attempt to trick users into replying to a text so that links are enabled again.
As you can see below, a fake USPS shipping issue and a fake unpaid road toll text were sent from unknown senders, and iMessage automatically disabled the links.
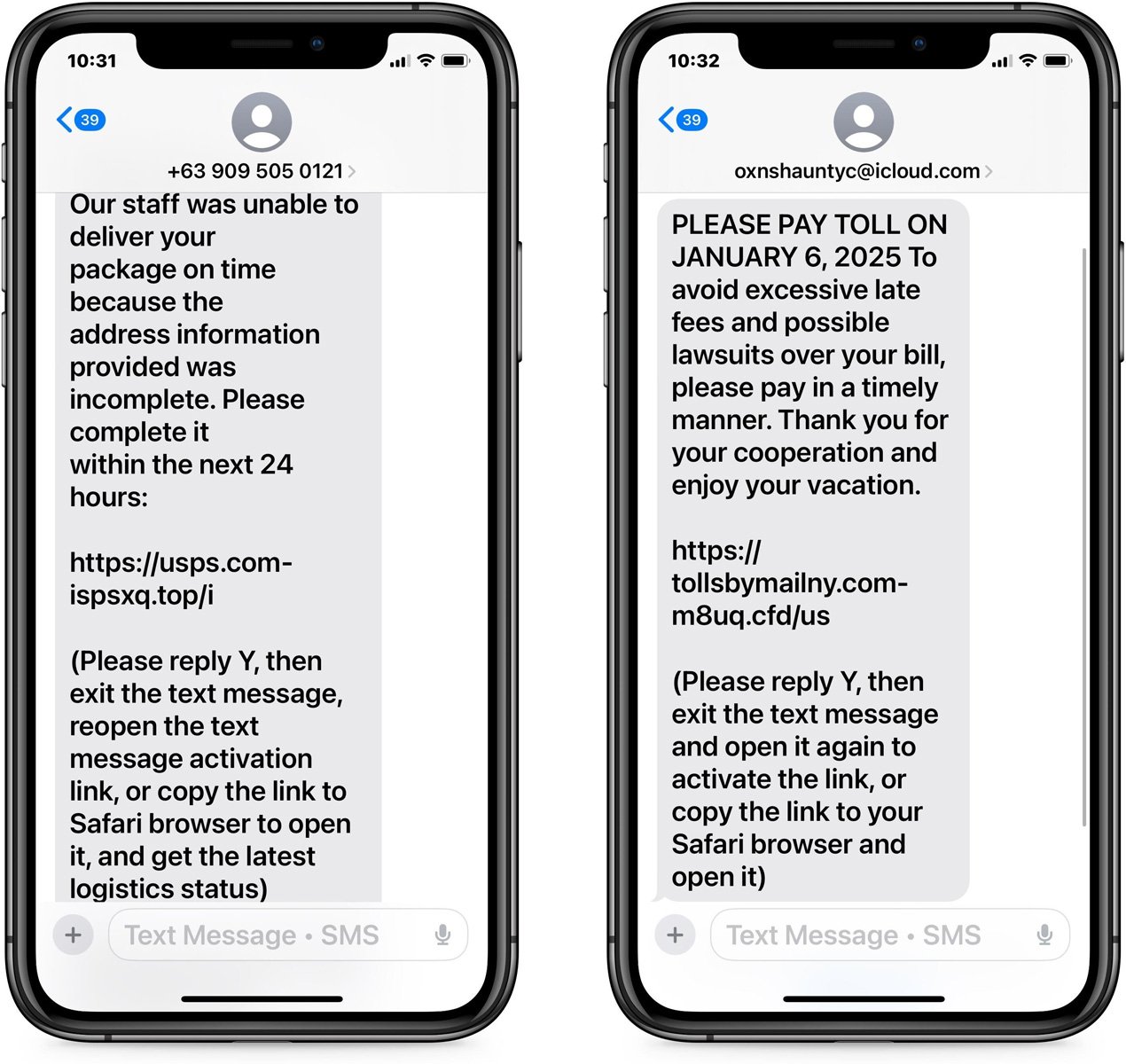
Source: BleepingComputer
While neither of these phishing lures is new, we noticed that these smishing texts, and others seen recently, ask users to reply with “Y” to enable the link.
“Please reply Y, then exit the text message, reopen the text message activation link, or copy the link to Safari browser to open it,” reads the smishing messages.
Further research shows this tactic has been used over the past year, with a surge since the summer.
As users have become used to typing STOP, Yes, or NO to confirm appointments or opt out of text messages, the threat actors are hoping this familiar act will lead the text recipient to reply to the text and enable the links.
Doing so will enable the links again and turn off iMessage’s built-in phishing protection for this text.
Even if a user doesn’t click on the now-enabled link, the act of replying tells the threat actor that they now have a target that responds to phishing texts, making them a bigger target.
While most of our regular readers will be able to spot that these are phishing attacks, BleepingComputer was shown one of the above texts by an older family friend, who was unsure if it was legitimate.
Unfortunately, these types of people are commonly the target of these types of phishing messages, leading them to enter their personal information, credit card information, or other details that the attackers then steal.
If you receive a message whose links are disabled or from an unknown sender asking you to reply to the text, you are strongly advised not to do so.
Instead, contact the company or organization directly to verify the text and ask if there is anything else you need to do.


