
CrowdStrike is warning that a phishing campaign is impersonating the cybersecurity company in fake job offer emails to trick targets into infecting themselves with a Monero cryptocurrency miner (XMRig).
The company discovered the malicious campaign on January 7, 2025, and based on the phishing email’s content, it likely didn’t start much earlier.
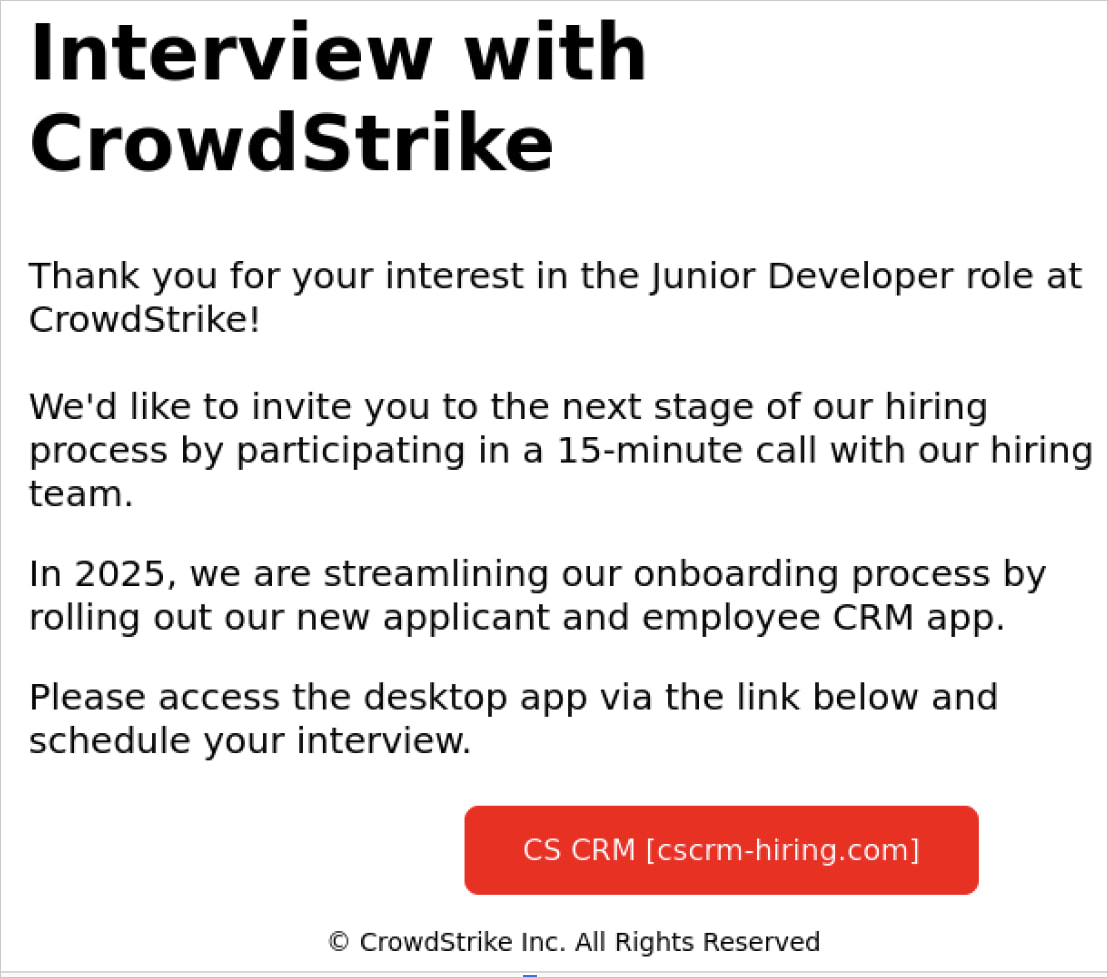
The attack starts with a phishing email sent to job seekers, supposedly from a CrowdStrike employment agent, thanking them for applying for a developer position at the company.
Source: Crowdstrike
The email directs targets to download a supposed “employee CRM application” from a website designed to appear like a legitimate Crowdstrike portal.
This is supposedly part of the company’s effort to “streamline their onboarding process by rolling out a new applicant CRM app.”
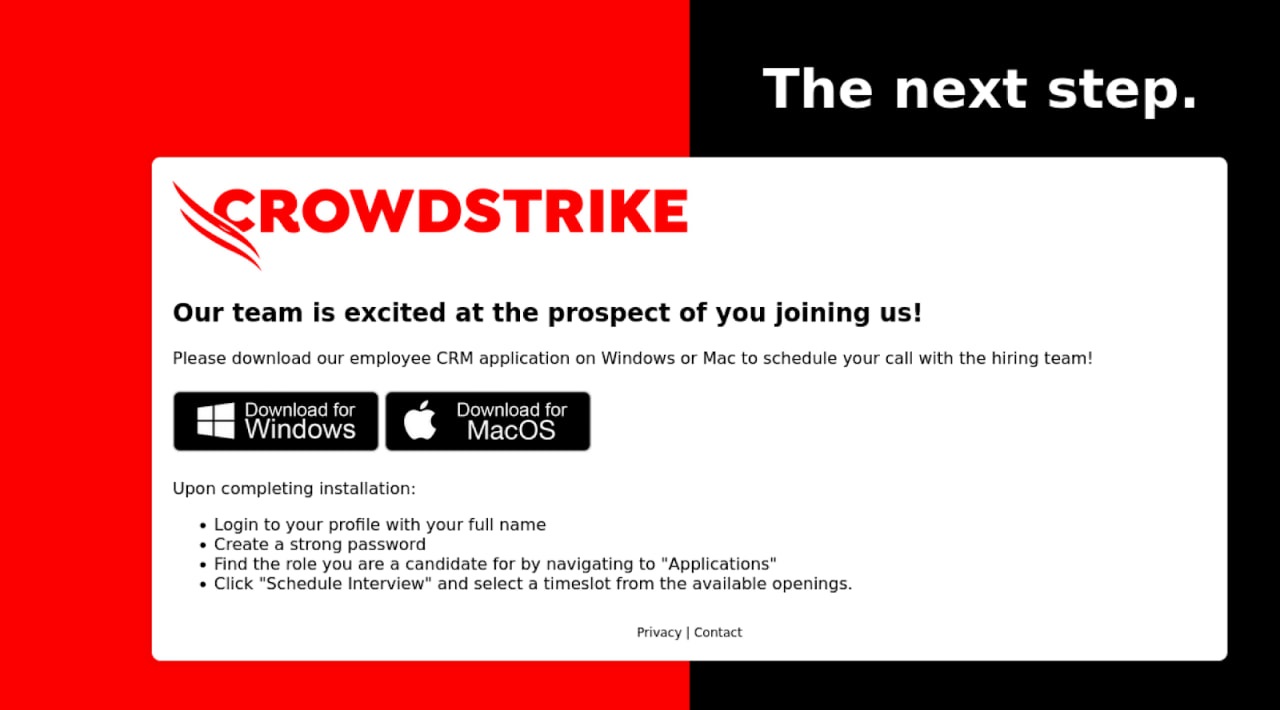
Candidates clicking on the embedded link are taken to a website (“cscrm-hiring[.]com”) that contains links to download the said application for Windows or macOS.
Source: Crowdstrike
The downloaded tool performs sandbox checks before fetching additional payloads to ensure it’s not running in an analysis environment, like checking the process number, CPU core count, and the presence of debuggers.
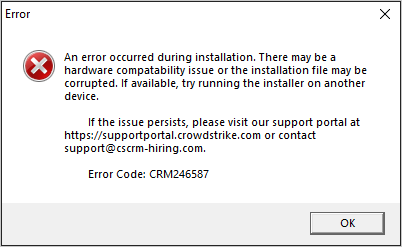
Once those checks are over and the result is negative, aka the victim qualifies for infection, the application generates a bogus error message informing that the installer file is probably corrupt.
Source: Crowdstrike
In the background, the downloader retrieves a configuration text file containing the required parameters for running XMRig.
It then downloads a ZIP archive containing the miner from a GitHub repository and unzips the files in ‘%TEMP%\System\.’
The miner is set to run in the background, consuming minimal processing power (max 10%) to avoid detection.
A batch script is added in the Start Menu Startup directory for persistence between reboots, while a logon autostart key is also written in the registry.
More details on the campaign and indicators of compromise associated with it can be found in Crowdstrike’s report.
Job seekers should always confirm they are speaking to an actual recruiter by verifying the email address belongs to the official company domain and by contacting that person from the official firm’s page.
Beware of urgent or unusual requests, offers that are too good to be true, or invitations to download executable files on your computer, supposedly required for recruitment.
Employers rarely, if ever, require candidates to download third-party applications as part of an interview process and never request upfront payments.


